What is E-Commerce Security?
E-commerce cybersecurity is the practice of safeguarding electronic commerce (e-commerce) systems and data from unauthorised access, use, disclosure, disruption, modification, or destruction. It is crucial for businesses that sell products or services online as it helps protect customer data and prevent fraud. The retail business has been one of the most targeted sectors for cyberattacks.
Like every industry, e-commerce has its set of standards and measures to uphold cybersecurity at its highest level. In this article, we will examine e-commerce security threats, solutions, security measures, standards, and best practices.
International Organisation for Standardisation (ISO)
The International Organisation for Standardisation (ISO) plays a significant role in e-commerce cybersecurity by developing and promoting international standards for securing e-commerce transactions. These standards ensure that e-commerce systems are secure and that personal and financial data is safeguarded from unauthorised access.
Some key ISO standards for cybersecurity in e-commerce include:
- ISO/IEC 27001:2013 – Information security management systems.
- ISO/IEC 27032:2023 – Cybersecurity — Guidelines for Internet security.
- ISO/IEC 27701:2019 – Information security management systems — Extension for privacy information management.
- ISO/IEC 15408 – Common criteria for information technology security evaluation.
These standards cover a wide range of topics, such as risk assessment, security controls, incident response, and data protection. Organisations of any size use them to protect their e-commerce systems and data.
Personal Data Protection
Personal data protection is vital for e-commerce cybersecurity. When customers shop online, they often provide personal information like name, address, email address, and credit card number. This information is necessary for completing transactions, but it is sensitive and can be misused if it falls into the wrong hands.
Several ways exist to protect personal information in e-commerce:
- Encryption. Encryption converts data into a scrambled format that requires a special key to read. This shields the data from unauthorised access during transit or while stored on a server.
- Access control. Access control restricts who can access the data by using passwords, two-factor authentication, and other security measures.
- Data backups. Data backups create copies of the data stored securely, offering protection in case of a data breach or disaster.
- Data minimisation. Data minimisation involves collecting only necessary data for a specific purpose, reducing the risk of data breaches and other security incidents.
By implementing these and other security measures, e-Commerce businesses can protect the data and reduce the risk of security breaches.
In addition to the technical measures mentioned above, several non-technical ones can be taken to protect customer’s data in e-commerce:
- Educating employees about data security. Employees should receive training on how to protect the data and identify/report suspicious activity.
- Having clear data security policy. Businesses should establish clear policy on collecting, using, and storing the data and communicate it to employees and customers.
- Responding quickly to security incidents. Businesses should respond promptly to security incidents to minimise damage, including notifying your customers, investigating the incident, and taking preventive measures.
User Authentication
User authentication is the process of verifying user’s identity before granting them access to a system or resource. In e-commerce, user authentication is essential for protecting personal information and preventing fraud.
There are several methods of user authentication, but here we will focus on the three main ones:
Multi-Factor Authentication (MFA)
MFA requires users to provide at least two methods to establish their identity before gaining account access. This additional authentication may include a one-time PIN, identity verification via a mobile app, answering a security question, or completing a biometric scan in addition to a login and password combination.
MFA helps prevent many security breaches. Businesses should ensure their employees use MFA and encourage your customers to do the same. Though seemingly time-consuming, it is significantly safer than using only passwords and far less time-consuming than dealing with a successful data breach.
Two-Factor Authentication (2FA)
2FA is a security process that requires two different authentication factors to verify a user’s identity. It adds an extra layer of security to traditional username and password authentication, making it more challenging for unauthorised users to access accounts.
In e-commerce, 2FA is often used to protect customer accounts and prevent fraud. For example, when a customer logs in to an e-commerce website, they may be asked to provide their username and password, as well as a code sent to their mobile phone.
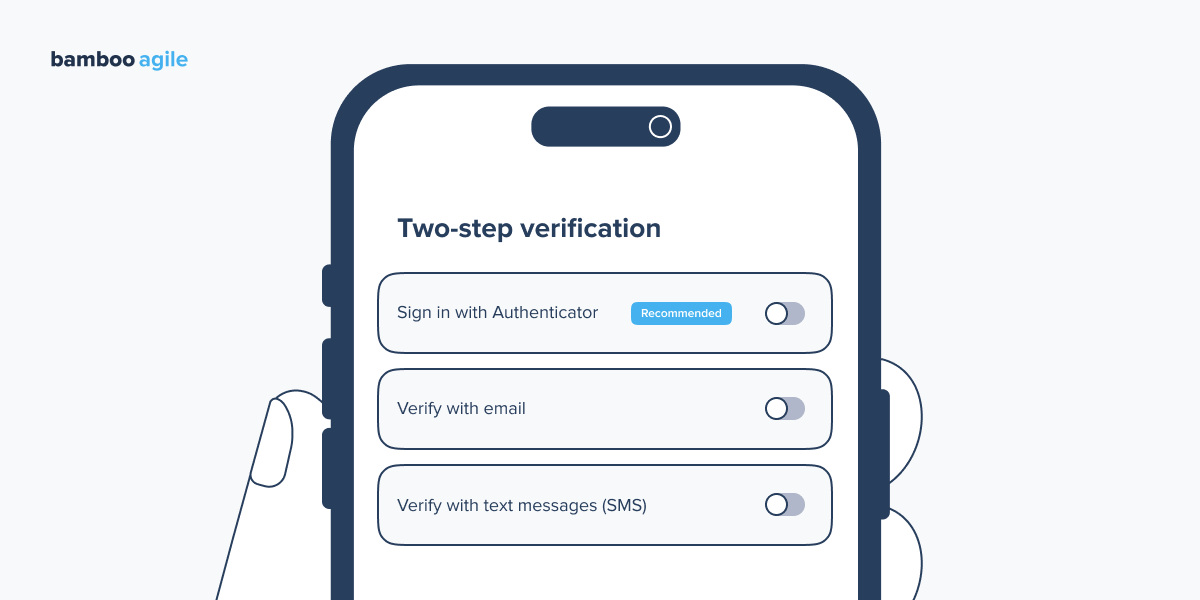
Two-Step Verification (2SV)
This type of multi-factor authentication requires two sequential authentication processes. For instance, Google employs 2SV. To log in, users enter their username and password, followed by a code.
It’s worth noting that 2FA and 2SV are both types of multi-factor authentication, which can also include three-factor authentication or three-step verification (or more). The fundamental difference lies in the type of authentication techniques used. If login is a two-step process, it will always be 2SV. If the two-step process uses distinct authentication factors, it’s a 2FA login.
Security Basics
You and your clients should never forget the basic things that keep your e-commerce website and data secure. Among many important factors, we’ve highlighted the most crucial ones.
Passwords
Many data breaches arise as a result of insecure access credentials. Therefore, organisations should encourage their clients and employees to use strong passwords and practice password hygiene.
A strong password should be at least eight characters long and include a mix of upper and lowercase letters, numbers, and symbols. Users should not reuse their passwords on other websites. To achieve secure, efficient password management, consider using a password manager tool to keep passwords strong, unique, and regularly updated.
Antivirus and Firewalls
Businesses can use low-cost software, such as anti-malware, antivirus, and firewall technology, to provide basic defences against external security threats.
AI and machine-learning technologies in the latest device protection systems provide ongoing tracking and immediate threat detection. This can be extremely valuable in blocking fraudsters’ attempts to obtain personal client data and make fraudulent transactions.
To enhance security, businesses should maintain firewalls that monitor and filter all network traffic attempts. A firewall is an essential network security feature because it prevents confidential information from leaving the network without the knowledge of network administrators, logs user behaviour, and prevents data alteration by hackers or malicious software.
Third-Party Risk Management
E-commerce enterprises must also manage third-party risks. The assault surface of a company is not restricted to the company itself. Its cloud-service providers, vendors, and business partners are all potential supply chain flaws.
Businesses must recognise, comprehend, monitor, and mitigate third-party risks, especially as many online shops rely on several third-party plugins for store operation. However, as firms grow in size, this can become a difficult chore to execute, particularly when hundreds or thousands of vendors and suppliers are involved.
Security Standards and Regulations Compliance
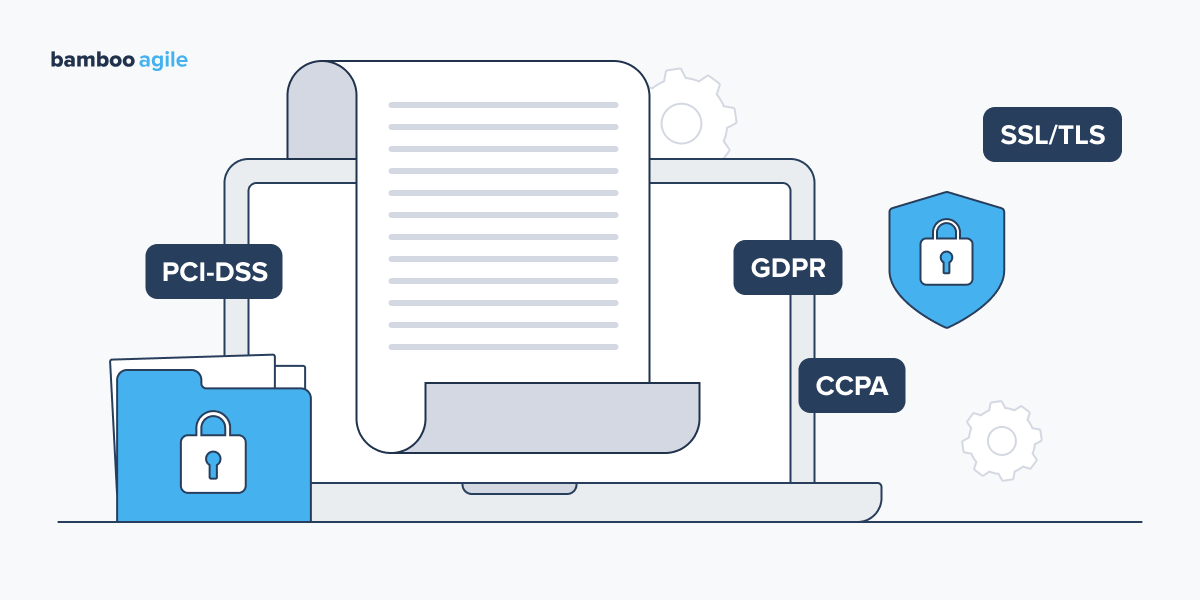
Earlier, we mentioned that e-commerce cybersecurity requires following standards and regulations. We’ve highlighted the most common ones.
Payment Card Industry Data Security Standard (PCI-DSS)
The Payment Card Industry Data Security Standard (PCI-DSS) is a collection of data security standards established by the Payment Card Industry Security Standards Council (PCI SSC). American Express, Mastercard, and Visa are among the members of this global forum.
The guidelines apply to any company that processes credit card operations, including the vast majority of e-commerce companies. The standards outline the minimal security criteria for safeguarding client credit card information.
While PCI-DSS is not the law, it is required under the main card payment brands’ contracts. Non-compliance with the security requirement can result in serious fines, such as a monthly fine ranging from £5000 to £100,000, as well as penalties from the acquiring bank.
General Data Protection Regulation (GDPR)
The General Data Protection Regulation (GDPR), unlike PCI DSS, is a European Union (EU) statute. Since 2018, every organisation that targets or gathers data on EU individuals has been subject to European Union (EU) privacy regulations.
GDPR compliance is a great strategy to safeguard your business from security dangers linked with e-commerce. The following are the fundamental principles of the GDPR:
- Minimisation of data
- Limitation of storage
- Integrity and confidentiality of data
GDPR requires organisations to gather as little data as possible, preserve it for as long as necessary, and safeguard it with the most up-to-date security. Each concept contributes to an organisation’s security posture, hence improving information security.
California Consumer Privacy Act (CCPA)
The California Consumer Privacy Act (CCPA) is a state law that gives consumers more control over their personal data. The CCPA went into effect on 1st January 2020, and applies to businesses that collect personal information from California residents.
The CCPA gives consumers the following rights:
- The right to know what personal information is collected about them
- The right to delete personal information
- The right to opt out of the sale of their personal information
- The right to non-discrimination for exercising their CCPA rights
The CCPA also requires businesses to take certain steps to protect consumer privacy, such as:
- Getting consent from consumers before collecting their personal information
- Providing consumers with clear and concise information about how their personal information is collected and used
- Allowing consumers to opt out of the sale of their personal information
Businesses that violate the CCPA can be fined up to £7,500 per violation, or up to £2,500 per unintentional violation.
The CCPA is comparable to the GDPR in that it applies only to the state of California. It is now the most stringent requirement in the United States.
SSL/TLS Certificates
HTTPS is a network protocol that encrypts and validates data transmissions, making it far more secure than HTTP. To provide greater security to its users, online companies that process sensitive information, including financial details, should always use HTTPS.
A Secure Socket Layer (SSL) certificate, which is code that permits encrypted communications, is required to perform HTTPS hosting, also known as Transport Layer Security (TLS).
With the installed HTTPS, hackers will find it much more difficult to access, read, or manipulate sent data, giving another layer of safety to companies and their customers.
E-Commerce Security Major Threats

Now that we’ve discussed many ways to protect e-commerce businesses’ cybersecurity, it’s important to mention the possible threats you may face.
Attacks, Malware, Ransomware Types
Distributed Denial of Service (DDoS)
DDoS attacks are used by cybercriminals to disrupt target organisations by assaulting their servers with requests to overload the systems. These attacks are typically coordinated by a single workstation that uses botnets, a network of malware-infected devices that overwhelm the target with requests.
Although DDoS assaults are not intended to steal data, they can dramatically harm companies for the sole purpose of causing commercial disruption. E-commerce enterprises that suffer operational disruption face huge losses, which may result in a full shutdown.
Malware
Malware refers to any harmful program attempting to infect a computer or mobile device. It is effective in obtaining personally identifiable information (PII), including access credentials, redirecting users to alternative web pages, stealing money, and blocking access to the site and systems.
Cybercriminals are drawn to e-commerce platforms because they can target an organisation’s clients with malware. They can accomplish this via modifying an e-commerce site in an XSS attack or by sending authentic-looking messages to customers using compromised access credentials, generally via email.
Ransomware
Ransomware is a type of malware that encrypts a victim’s files and demands a ransom payment to decrypt them. Ransomware attacks are on the rise, and they can be devastating for businesses and individuals.
Ransomware attacks typically start with a phishing email or malicious website that infects the victim’s computer with malware. Once the malware is installed, it encrypts the victim’s files and displays a message demanding a ransom payment. The ransom payment is typically demanded in Bitcoin or other cryptocurrency, and the amount of the ransom can vary. If the victim does not pay the ransom, the files will remain encrypted and may be lost forever.
Phishing
Phishing is the most common attack vector for most firms, including e-commerce. Customers at e-commerce stores are in danger of being targeted by phishing or social engineering. These attacks are often carried out through the use of fake messages aimed at misleading recipients into providing personally identifiable information such as passwords, account numbers, and payment information. This information can be used by cybercriminals to gain unauthorised access to one or several user accounts.
One of the most serious security concerns about phishing is that an effective attack may result in a large data breach and the disclosure of access credentials on the dark web. A successful phishing attempt is a common precursor to malware infestation.
SQL Injection
While keeping information in a Structured Query Language (SQL) server database is common, it is not always secure. SQL servers hold data in a sequence of tables, which applications can access via requests or “queries.” If these servers are not protected, hackers can write and insert their queries, granting them access to read or edit any data in a SQL database.
To protect against SQL injection (SQLi), it’s essential to give your developers security training, treat any changes to data tables as untrusted, and implement modern web development technologies.
Cross-site Scripting (XSS)
XSS attacks are a sort of malicious code insertion on an e-commerce website. These assaults occur when a hacker utilises a web application to convey malicious code, exposing users to cyberattacks.
Visitors to the web page are immediately infected with the virus. Unprotected public discussions, message boards, and online pages that enable user comments are the most popular targets for an XSS attack.
E-skimming
E-skimming is a significant security concern for e-commerce companies because it involves fraudsters recording information that customers type into their online checkout pages in real-time. They often get access to the online store through a successful phishing attempt, though XSS, third-party compromise, and brute force assaults may also be used.
Once in the system, the cybercriminal can insert malicious skimming code that either sends clients to a fake website, or directly collects credit card data in real-time.
E-Commerce Security Best Practices
Now let’s look at some best practices for e-commerce website owners to protect businesses from cyberattacks.
HTTPS Authentication
As we wrote above, Hypertext Transfer Protocol Secure (HTTPS) is a secure version of the Hypertext Transfer Protocol (HTTP) that encrypts data sent between a web server and a web browser. This encryption helps to protect sensitive data, such as credit card numbers and passwords, from being intercepted by unauthorised third parties.
There are many benefits in using HTTPS for e-commerce websites, such as increased security, improved customer trust, and increased search engine rankings.
Plugins and Third-Party Integrations Review
Take an audit of the third-party systems in your technology stack and confirm that they are properly up to date. Determine the security of each, and confirm that it meets your security criteria and standards.
Site Up-to-Date Provision
Your website’s software will almost certainly receive regular upgrades and patches, which will provide enhanced security. Ensure that everything is updated as needed.
Regular Data Backup
Backups must be made regularly to guarantee that the data is relevant and capable of keeping the organisation operational during an urgent crisis. To guarantee that the backup is not affected by network issues, it should be stored away from the core networks, such as with a secure cloud storage service provider.
Strong & Unique Passwords Implementation
One of your most critical defences against cyber attackers is a strong and unique password. Creating a passphrase or a strong password keeps your website and information safe from hackers.
Only Key Customer Data Storage
Less information reduces the risk of data breaches, therefore organisations should only acquire vital data required to perform activities. For example, organisations do not need to gather customer’s full date of birth, and can instead use a month and day, or a month and year.
Organisations could also use compliance verification, such as a know-your-customer (KYC) framework, to reduce the quantity of data they store. KYC checks users’ input, verifies the information, and confirms their identity using third-party sources, then maintains little to no actual data.
Device Protection
To avoid being abused by vulnerabilities, all devices and software should be updated regularly. Unpatched devices and applications may be unable to protect against the most recent threats and vulnerabilities.
The majority of software upgrades are security-related. Checking for and applying updates regularly delivers potentially critical security patches, repairing flaws that fraudsters could otherwise exploit.
Social Engineering Attempts Protection
Social engineering occurs all the time, and it is the company’s responsibility to train and advise its employees on how to avoid attacks. Companies conduct phishing tests on their staff regularly to evaluate how vulnerable they are to such assaults.
Regular PII Audits
A smart e-commerce cybersecurity strategy includes three critical steps: defining what personally identifiable information relates to your company, determining how it is stored in an encrypted state when at rest, and determining how data is encrypted when in transit. The approach should include establishing an internal subject matter expert to lead this programme, raising employee knowledge of PII, conducting regular audits, and optimising to keep current.
Proper Key Management
It is critical to use proper key management. The most serious issue that businesses face today is the revealing of private data when compromise happens, and the reason for this is that everyone is focused on encryption solutions. Most regulations require encryption of essential and/or personal information, which most businesses do; nevertheless, they don’t even mention key management.
Robust Data Security Tool
E-commerce businesses manage significant volumes of sensitive data, such as personally identifiable information, which makes them vulnerable to fraudsters. Furthermore, the enormous number of transactions, as well as the utilisation of numerous cloud platforms, can generate further vulnerability. As a result, companies require a strong data security platform that gives them total visibility into their general data security situation, including data consumption and access inventories.
Encryption Everywhere Principle
Begin with HTTPS both within and outside of your microservice; this ensures all information in transit is encrypted. The common advice is to keep the information encrypted until it is ready to be analysed or displayed. Rotate the encryption keys regularly, and don’t preserve data forever—archive it if necessary, using an alternate encryption key for each stage.
Cybersecurity Awareness and Training
Human mistakes are frequently the first point of entry in many security breaches. Retailers should provide cybersecurity training to all staff to build robust defence against cybercrime. Furthermore, depending on their risk exposure, various groups should receive distinct training.
A longer-term answer would be to create a cybersecurity culture. This goes beyond cybersecurity training since it starts with growing knowledge and authentic participation in cybersecurity strategy at the board level and then spreads throughout the organisation.
E-Commerce Security During Holiday Season

A strong customer experience is crucial for any e-commerce organisation, especially during this holiday season. To make sure your e-commerce site is prepared to face the holiday rush, it must be safe.
Pre-holiday Security Check
Here is a security checklist to help you prepare for the holiday season:
- Make sure the connection is secure. Check that your store’s secure connection settings are enabled, and that it works through the HTTPS protocol.
- Check your users. Examine your store’s Administration panel for any unexpected new admin users. An attacker could set up a new admin user using a hijacked user account.
- Withdraw outdated permissions. Withdraw outdated permissions, as outside suppliers and employees may retain access to critical areas of your website even after their work is done or they leave the organisation.
- Use stronger passwords. Make administrators and customers use stronger passwords. A password that is at least 12 characters long, random, and contains a wide pool of characters will be extremely tough to crack. Limit the number of unsuccessful login attempts that a bot can make before being locked out.
- Enable reCAPTCHA. In your store, enable the reCAPTCHA add-on. It uses a free Google service to identify harmful traffic on your web page with minimal user interaction. ReCAPTCHA employs an advanced risk analysis algorithm and adaptive challenges to prevent automated software from performing abusive activities on your site while allowing legitimate users to pass through with ease.
- Look at your frontend. When was the last time you went through your site’s front-end or even looked at your homepage? As busy site owners, we most likely connect straight to our sites’ backends to add new products, content, and do site maintenance. Running through the pages and items on your website can help you spot signs of infection: changes on your homepage, malicious pop-ups, spam, and unexpected redirects.
- Check your third-party extensions. Third-party add-ons are safe to use if the versions are officially supported. Unofficial themes and plugins that are readily available may have secret, back-door routes that hackers can use to infiltrate and harm your e-commerce site.
- Check your site speed. An infected site may feel sluggish, and it can experience slowdowns due to brute force assaults or malicious scripts using server resources. Examine page loads for every part of your site, from the time it takes an image to render to the speed of the checkout process.
- Make a backup. Data loss as a result of cyber-attacks is not unusual. Even if you don’t backup your data regularly, you risk losing it forever. However, if you use a managed e-commerce web hosting provider, such as AWS hosting, you will definitely avoid this problem.
Fraud Protection Increase
Because of relying on untrustworthy third-party solutions, many e-commerce sites are inherently unsafe and prone to attack. As a result, client-side security is a weakness for many e-commerce sites, allowing security problems to occur in the browser without the customer’s knowledge.
Attackers can exploit client-side security flaws through e-skimming, formjacking, or cross-site scripting. Customer data, such as credit card numbers, personal information, and login passwords, may be compromised as a result of these attacks. They can also result in financial losses for the e-commerce company as well as potential regulatory compliance issues.
Customer Service Team Alert
Threat actors engage in refund fraud attempts to get false reimbursements for goods by taking advantage of merchants’ return policies, customer support employees, and third-party affiliates. Customer service teams should be aware of such causes not only to prevent fraud but also to help their real customers avoid fraudsters.
Security Update Plan
Your storefront should be code-frozen at least two weeks before the holidays, but not your security. Check your website for vulnerabilities and keep it up to date.
Security and Privacy by Design
“Privacy by design” suggests that you do not endanger the organisation by collecting or processing data in a way that could result in a privacy violation. Data, for example, should be encrypted both at rest and in transit, with the key stored with the user. The processor will not have access to the data unless the user is involved and consents to the transaction.
Data Management Principles
Here are some of the main data management principles for ensuring e-commerce cybersecurity:
First-party Data Management Focus Principle
E-commerce businesses should consider how they create, manage, and own first-party data to guarantee that it is secure and that they are in compliance with local laws around the world. Continuing to focus on third-party data strategies or developing data partnerships that expose consumer data should be avoided.
Business-Critical Data Only Storage
E-commerce businesses must build their cybersecurity plans on a complete data inventory, reevaluating the data they have regularly, and regularly assessing their security posture over time. Storing and protecting just business-critical data while removing unnecessary information minimises risk, improves performance, and reduces environmental impact.
Data Rationalisation Principle
Data rationalisation is simple. Only save data that your company may assign a monetary value to. You do not have to safeguard data that you do not keep. Weigh the worth of data with a specified value against the expense of keeping it secure, the required cyber insurance, and the costs of a breach. If the fee exceeds the value, get rid of it.
Secure Infrastructure
The three things e-commerce businesses must consider are:
- Whether they need the data.
- How it’s going to be stored and whether it will be encrypted.
- How they will prevent hostile actors from accessing the data.
E-commerce businesses must employ or construct secure software services by subscribing to an external service or building it in-house.
Post-Quantum Cryptography – Pros and Cons
Post-quantum cryptography (PQC) is a type of cryptography that is designed to be secure even against quantum computers. Quantum computers are still in their early stages of development, but they have the potential to break many of the encryption algorithms that are currently used to protect data.
PQC is a promising solution for the future of e-commerce security. It can help to protect customer data from unauthorised access, even if quantum computers become a reality.
But what about the pros and cons of PQC in e-commerce?
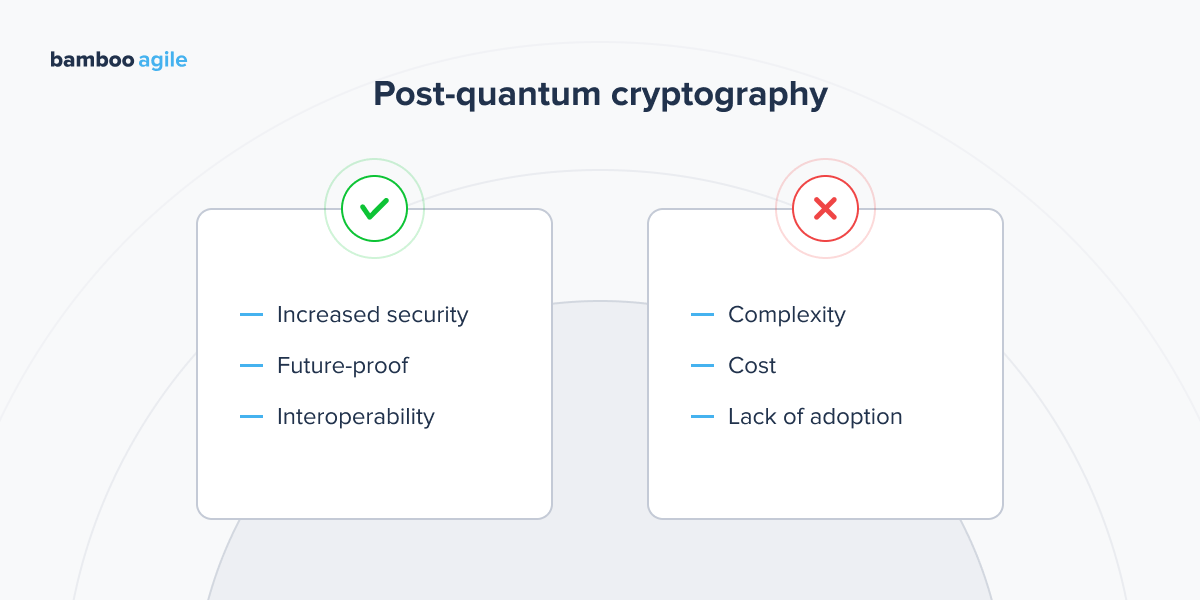
Pros:
- Increased security. PQC is designed to be secure against quantum computers, which means that it can help to protect customer data from unauthorised access.
- Future-proof. PQC is a forward-looking technology that can help to protect data from future threats.
- Interoperability. PQC is designed to be interoperable with existing cryptographic algorithms, which means that it can be used to secure existing e-commerce systems.
Cons:
- Complexity. PQC algorithms are more complex than traditional cryptographic algorithms, which can make them more difficult to implement and use.
- Cost. PQC algorithms can be more expensive to implement than traditional cryptographic algorithms.
- Lack of adoption. PQC is still a relatively new technology, and it is not yet widely adopted. This means that there may be compatibility issues with existing e-commerce systems.
PQC is a promising technology for the future of security for e-commerce. It offers increased security and future-proofing, but it is also more complex and expensive than traditional cryptographic algorithms. As PQC technology matures and becomes more widely adopted, it is likely to become a more common security measure in e-commerce.
How Bamboo Agile Helps Secure Your E-Commerce Website
As you can see, the store owner’s attentiveness is crucial for store safety, yet it is insufficient.
When it comes to cybersecurity, your e-Commerce software development and hosting service provider are more important than you might consider. In reality, if you choose an untrustworthy supplier, you expose your site to exploitation and downtime.
If you entrust your website to our skilled staff, you value perfection. We continually scan the servers for flaws and follow as many cybersecurity practices as possible to ensure the security of your e-commerce store. As a result, our clients are fully protected against cyber threats.
To ensure your e-commerce store is in the safe zone and not facing any threats, contact Bamboo Agile’s team of professionals for a free consultation. Your website cybersecurity is our top priority.