Introduction
Continuous integration, delivery, and deployment are software development approaches that emerged from the DevOps ideology. It improves the efficiency of code development, testing, and release, as well as the speed with which working products are delivered to users. When done correctly, a build pipeline allows teams to quickly release working software while also receiving fast feedback on their most recent modifications.
Building a pipeline for Continuous Integration and Continuous Delivery (CI\CD) should not be treated as an afterthought. It helps to take an iterative strategy for your CI/CD processes, just as it does with software development: continually analysing data and listening to comments to improve your CI/CD process. In this article, we will look at the best practices of continuous integration and delivery that you should think about using in your pipeline.
What are the best practices for CI/CD?
Choose a Reliable and Scalable CI/CD Platform
The platform you choose for operating your CI/CD pipelines is going to be around for a long time, so it’s critical to assess your options and how they meet your needs. A CI/CD platform should at least provide:
- Reliability. Continuous improvement is the beating heart of your growth initiatives. You’re out of luck if it goes down. If that happens, you won’t be able to receive comments and feedback or release new software.
- Speed. You should see the outcome of your latest build in 5 to 10 minutes.
- Scalability. Your pipeline should expand in tandem with the project. Your platform should be scalable.
- Easy to use. CI pipelines should be simple to set up and alter. It should also be straightforward to debug build issues or test failures.
Set up CI/CD Access
Granting access to your CI/CD pipeline requires a balance between enabling efficient development and maintaining security.
The implementation of role-based access control allows you to define specific permissions for different user roles (developers, testers, admins) and give users only the access they need for their tasks. You can also use service accounts instead of personal ones for tasks executed within the pipeline. These accounts have specific scopes and expire automatically, reducing risk of unsolicited access.
You can secure your infrastructure by:
- Isolating and hardening the CI/CD server. Run the CI/CD server on a separate network segment with restricted access. Implement strong firewalls and intrusion detection systems.
- Using secure containers or VMs. Run pipeline jobs in isolated containers or VMs to prevent lateral movement of attackers.
Avoid storing secrets in plain text. Instead, use secrets management tools that store credentials securely and encrypt them at rest and in transit. Also, rotate secrets regularly and change them periodically to minimise the impact of potential leaks. Consider using short-lived credentials for specific jobs.
Another important thing is monitoring and auditing access. Track user activity and pipeline execution for potentially suspicious behaviour and add an extra layer of security by requiring a second factor (like a code from an authenticator app) for logins.
Set up Security and Provide Regular Security Scanning
A CI/CD system designed using continuous integration best practices gives access to the code base and passwords for deployment in multiple environments. As a result it is frequently subject to cybersecurity risks. This means you should isolate your CI/CD systems and keep them in secure internal networks/storage.
VPNs, multi-factor authentication, and identity & access management solutions can all aid you in safeguarding that data. For starters, you should avoid storing any secrets on the CVS. Next, you can containerise your agents and deploy them over secure networks. And naturally, you should ensure that security is a top priority throughout the development process. This is frequently referred to as DevSecOps.
Basically, security tests are critical in a pipeline developed following CI/CD best practices. They involve scanning the containers, checking the code for grammatical and formatting mistakes, and looking for potential errors.
Provide Continuous Testing and Fix the Found Issues
Continuous testing allows teams to include automated feedback throughout the software development life cycle (SDLC). It aids in shifting testing to the left, ensuring that teams receive feedback earlier in the SDLC cycle when issues are easier and less expensive to resolve.
Continuous testing is an essential component of continuous integration and delivery/deployment pipelines. It gives fast feedback to help improve code quality, shorten SDLC times, prevent bottlenecks, and speed up DevOps processes.
The majority of your testing should be automated. Human intervention should not be required. Ideally, tests should run whenever you save a file on your development workstation or commit changes to the repository.
The convenient thing here is that every language has numerous testing frameworks to select from. Most allow you to trace file changes and re-run tests as needed. This creates a speedy feedback loop that improves consistency and will most likely save developers hours each week.
All in all, continuous integration cannot be achieved without automation.
Choose Between Branching and Trunk-Based Development
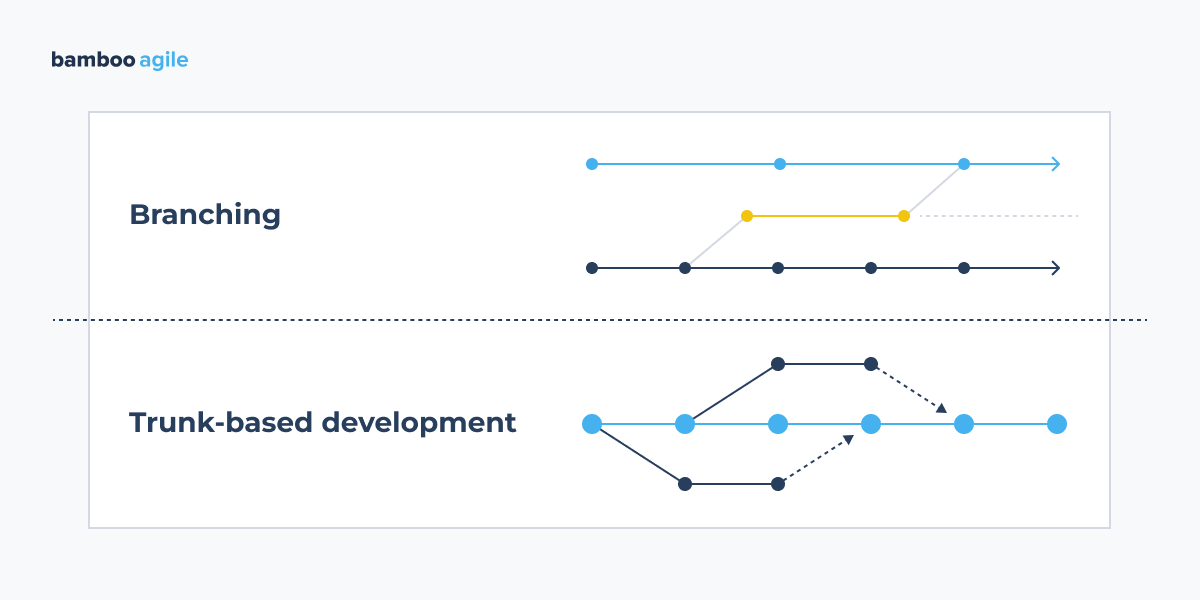
Trunk-based development is an approach to programming that aims to keep branches as small as possible. This method involves developers working on a single primary (or master) branch known as the trunk. Branches can be formed as long as they do not last longer than a few minutes or some hours, and never more than a day. They must be merged into the trunk (or rejected) as soon as possible to keep the codebase stable and releasable.
Long-lived branches, such as feature branches, can complicate development in a variety of ways. The most problematic concerns they cause include:
- Information obscuring: teammates are unable to see what you’re working on, limiting collaboration.
- Merge conflicts: these conflicts might result in unexpected delays, blocking you from releasing new features on time.
- Extra work: The longer a branch exists, the more effort will be required to combine it with the trunk.
Keeping the branches as small as possible provides two benefits. First, we avoid the issues that long branches cause. Second, short branches naturally encourage working in modest, safe steps.
Branching strategies, like tabs versus spaces, are emotionally charged topics that spark passionate online and offline disputes.
While many people have strong ideas on the optimal strategy, as with many aspects of software development, the correct answer is context-dependent. With that in mind, let us look at what branching techniques are and how they relate to CI/CD.
To put it simply, a branching strategy is your team’s agreement on how and when to generate and merge branches in version control. How you build up your version control system and use branches will influence how you set up your CI/CD pipeline, so select a model that matches your requirements best.
Branching in Version Control Systems
Branching methods became important for development teams as distributed version control systems gained popularity, making this approach easier.
With distributed systems, the repository has numerous copies, resulting in multiple sources of truth. So the team works on modifications in parallel on separate copies of the repo, sharing progress by pushing changes to other copies of the same repository.
Git simplified the process of creating branches and merging commits from several branches. In Git, a branch is just a commit (or a series of commits) marked with a specific name. Branches are great for containing a series of changes, such as work on a new feature or a rogue experiment.
You can share the modifications by moving the branch to another repository and/or merging it with a different branch, such as the master one, to integrate it into the rest of the codebase. You can also undo the adjustments if you decide against them. When you merge two branches, Git takes care of matching the commits on each one, eliminating most of the hassle associated with merging in conventional version control systems.
Branching for CI/CD
The goal of continuous integration is to get everyone on the development team to commit changes frequently. This means you can routinely test that everything works as intended, rather than spending several weeks or months merging multiple work streams after the development is finished. As a result, software changes can be released more often, allowing for all the advantages of continuous delivery and deployment.
Branching is used in conjunction with CI/CD to determine where changes should be submitted, when automated tests and builds should be run, and where updates should be distributed. The most basic strategy is to avoid branching entirely. In trunk-based development, everyone contributes changes regularly to the master branch of a central repository, which is kept releasable and routinely deployed to production.
Trunk-based development can be quite effective, especially if you have a sophisticated CI/CD infrastructure and are doing continuous deployment to a hosted system, but it does present certain problems. Branching techniques offer multiple approaches to managing code changes, each with its own set of advantages and cons. The following are some of the most frequent tools used by development teams running CI/CD.
Feature Branches
As the name implies, feature branches are used to maintain certain features apart from the rest of the software. Keeping work in progress out of the master branch makes it easier to keep the master in a deployable state, and if you’re deploying straight from the master rather than a release branch, you minimise the risk of unfinished functionality being pushed to production. You can still share your work with all members of your team by pushing your branch to the central repo (if you’ve designated one) or to any other repository.
The main drawback of feature branches, which is frequently criticised by supporters of trunk-based development, is that by postponing the implementation of changes until the feature is “complete,” you miss out on the benefits of continuous integration. This increases the chance of merging conflicts and introduces more complicated defects that take longer to resolve than if changes were committed iteratively.
You can prevent these difficulties by configuring your CI server to execute automated builds and tests on both feature and master branches (or whatever branch you use to prepare releases). This guarantees that you receive rapid feedback on what has been built, while also lowering the likelihood of issues emerging when merging changes.
One strategy for reducing merge conflicts is to make feature branches short-lived, no more than a day or two. Another solution is to rebase the branch on top of the master or merge modifications from it regularly. This updates your feature branch with all the other changes being pushed to the master. However, if you have a large number of concurrent feature branches, each delaying commits to master, there is still a possibility of conflict.
Release Branches
Whereas feature branches oversee work in progress, release branches “harden” changes before they are released. Release branches are ideal for a continuous delivery approach, in which updates are sent at regular intervals rather than as soon as they are ready, and make it easier to handle several versions in production.
With a release branch procedure, after the modifications planned for a specific release are complete, a release branch containing the relevant changes is generated, and no new additions are merged in. Meanwhile, features planned for future releases can continue to be integrated into the master or elsewhere.
Release branch builds then go through a set of automated tests, and any bug patches are applied to the release branch, followed by additional rounds of testing until you’re ready to release. Those problem patches should also be pushed back to the main branch to ensure they appear in future product versions.
Keeping your release branches open for as long as necessary to support each version of your software makes it considerably easier to publish changes to older versions.
When an update is required, it can be created in a hotfix branch or on master, tested as usual, and then pushed to the release branch.
It will then go through the CI/CD pipeline on that particular branch to confirm that no issues exist before deploying the update. Alternatively, you can complete the work on the release branch and apply it to the master as needed.
Hotfixes
Hotfix branches function similarly to feature branches, although it’s worth noting for completeness. A hotfix branch seeks to deliver a problem patch into production as soon as possible.
Depending on where you deploy, you can establish a hotfix branch from either the master or the release branch. As with feature branches, you may want to run some of the CI/CD elements on your hotfix branch before merging it into the release or master branch, where it can go through additional automated testing before release.
Cut Down the Number of Builds
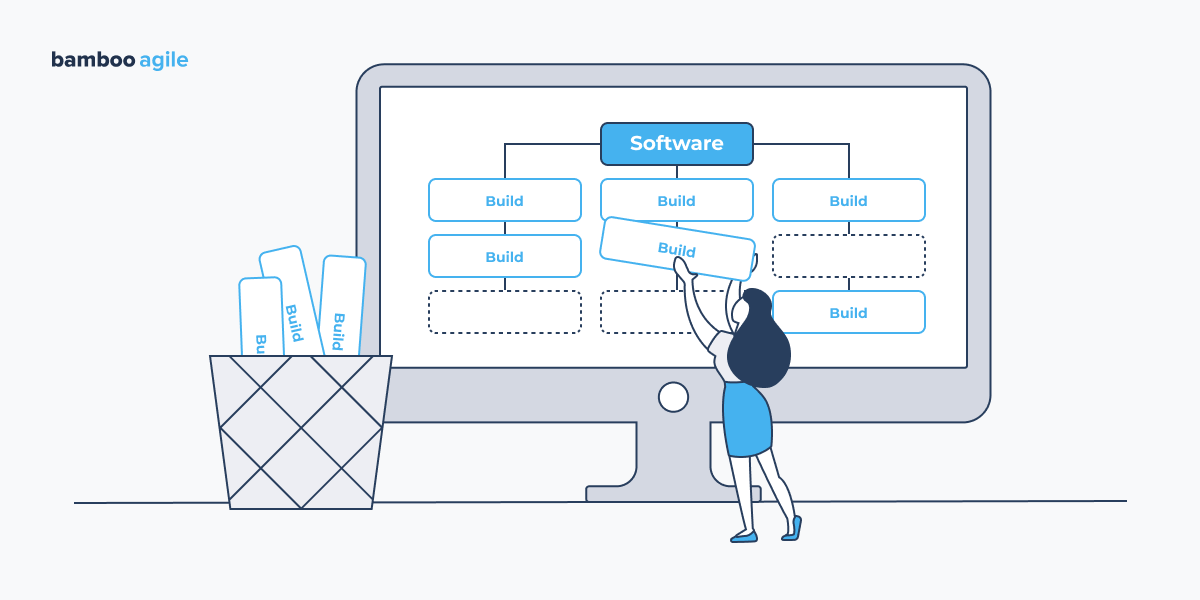
A typical mistake that appears rational at first glance is to create software for each phase of your CI/CD pipelines. A typical pipeline will include several different phases. The beginner’s method is to create a software artefact at the start of each phase. In theory, that seems right. You want a clean, new software package at each step. In practice, this frequently results in strange behaviours and situations that are difficult to grasp. This is because artefacts built on one stage may differ slightly from those built on another stage.
How is this possible? Assume you’re building a docker image at each step. Your docker image will be built around a base image. If you do not lock the version of that picture, the base image may be modified in the meantime. The same goes for any software that you install in the container. As a result, always build once and reuse the same artefact across the entire pipeline run. So, don’t establish distinct staging and production environments at every phase.
Make Your CI/CD Fast and Easy
The performance and usability of your CI/CD workflow are extremely crucial. If your pipeline is slow or difficult to use, your engineers will attempt to cut corners and avoid it wherever possible. Nothing is more aggravating than having to wait 30 minutes or more for your CI/CD pipeline to even begin building if you simply want to test a minor update. And the more developers attempt to skip the pipeline, the more likely it is that errors and problems will get through. This will result in a lack of trust in the entire process and a failure to get the benefits that you deserve. Make your CI/CD server or service as responsive and simple as possible.
Test Each Build Before Moving to Production
Testing ensures your software functions as expected and identifies potential issues before they reach users. Here are some best practices for integrating testing into your CI/CD pipeline.
Types of testing:
- Unit tests ensure individual units of code function correctly.
- Integration tests verify different parts of your code work together seamlessly.
- Functional tests confirm the software behaves as intended from a user perspective.
- Performance tests assess the software’s speed, scalability, and resource usage.
- Security tests scan for vulnerabilities and potential security risks.
Additional best practices:
- Define clear testing criteria and metrics. Know what you’re testing for and how well the tests are performing.
- Consider different testing environments. Test in environments mirroring production as closely as possible.
- Involve testers throughout the process. Collaborate with testers to define test strategies and review results.
By testing each build thoroughly before moving to production, you can significantly improve software quality, reduce rework, and deliver a better user experience.
Such an approach is crucial for CI/CD pipelines for several key reasons:
- Catching bugs early. Testing identifies potential issues early in the development cycle when they are much easier and cheaper to fix. This avoids costly bug fixes in production after release, potentially causing downtime, revenue loss, and reputational damage.
- Ensuring quality and functionality. Comprehensive testing verifies that the built software functions as intended and meets user expectations. This helps guarantee a high-quality user experience and prevents negative feedback or abandoned usage.
- Maintaining stability and security. Testing uncovers security vulnerabilities and potential stability issues before they reach production. This reduces the risk of security breaches and system crashes, protecting sensitive data and ensuring smooth operation.
- Faster feedback and iteration. Automated testing within the CI/CD pipeline provides rapid feedback on code changes. This allows developers to identify and fix problems quickly, iterate faster, and release new features more efficiently.
- Building confidence and reducing risk. Thorough testing instils confidence in the developers and stakeholders about the software’s quality and stability before deployment. This reduces the risk of production failures and unplanned downtime.
Implement the Results
Testing identifies issues, but fixing them and improving your software requires effective action. Here are some tips for implementing test results in your CI/CD pipeline.
- Ensure that the test results are clear, concise, and actionable. Developers need to understand what’s wrong and how to fix it.
- Prioritise issues based on severity and impact. Fix critical issues first to minimise risk and improve quality faster.
- Connect test results to code changes. Track which changes introduced each issue for efficient debugging.
- Automate fixes where possible to save time and improve consistency. To do so, implement auto-remediation for common, well-defined issues. You can also integrate static code analysis tools to automatically identify and fix potential issues early in the development process.Communicate test results effectively to developers and stakeholders. Keep everyone informed about progress and potential risks.
- Use issue-tracking systems and dashboards to manage and track the resolution of identified issues.
- Promote a culture of learning and improvement. Use test results to identify areas for improvement in development practices and testing strategies.
By effectively implementing test results, you can close the feedback loop, continuously improve your software quality, and build more reliable and secure applications.
Check the Environment
To get the most out of your QA suite, make the effort to clean up your pre-production settings in between deployments.
When environments are maintained running for an extended period of time, it becomes more difficult to track all of the configuration changes and updates that have been performed to them.
Settings drift away from the initial arrangement and from one another over time, so tests that pass or fail in one may not return the same result in another. Maintaining static environments also incurs maintenance costs, which can slow down the QA process and delay the release process.
Using containers to host environments and perform tests makes it simple to spin up and tear down for each new deployment, as these operations can be scripted using an infrastructure-as-code approach. Instantiating a new container each time preserves consistency and makes scaling environments easier, allowing you to test multiple builds in parallel if necessary.
Deploy in Production
Once you’ve invested in developing a dependable, fast, and secure CI/CD pipeline that gives you assurance regarding the quality of your builds, you don’t want to undermine that effort by enabling the process to be bypassed for any reason.
Typically, a request to bypass the release process is made because the modification is minimal or urgent, but giving in to such demands is a false economy.
Skipping the automated quality assurance stages increases the danger of introducing preventable defects. It also makes replicating and debugging issues significantly more difficult because the build is not easily deployable to a testing environment.
You will likely be asked to shortcut the process “just this once”. You’ll probably be in full firefighting mode at the time. However, it’s important to conduct a retrospective or post-mortem to determine the motivation behind that decision.
Is the process too slow? Perhaps there are some performance enhancements or refinements that need to be done. Is there a misunderstanding about when it should be used? Communicating the benefits of a CI/CD pipeline can help stakeholders buy in and avoid similar requests the next time the roof catches fire.
Post-Deployment Tests
While pre-deployment testing is crucial, it’s not foolproof. Unexpected changes in the production environment, configuration issues, or even external factors can still lead to problems. That’s where post-deployment tests come in as a best practice of CI/CD.
What are post-deployment tests?
These are tests executed after the software is deployed to production. They verify that the new version functions as expected in the real-world environment, catching issues that pre-deployment tests might have missed.
Types of post-deployment tests:
- Smoke tests. Basic checks to ensure essential functionalities are up and running.
- Performance tests. Monitor website or application performance under a real-world load.
- Security scans. Scan for vulnerabilities introduced during deployment.
- User Acceptance Testing (UAT). Involve real users to test for usability and functionality in the live environment.
- Synthetic monitoring. Simulate user interactions to continuously verify key functionalities.
Benefits of post-deployment testing:
- It can uncover problems specific to the production environment or user interactions.
- Verifies successful deployment and functionality before full user exposure.
- Quickly identifies and reverts to the previous version if issues arise.
- Detects problems early, limiting potential downtime and user impact.
- Provides valuable insights for future code changes and deployments.
However, remember, that post-deployment tests should complement pre-deployment testing, not replace it. Together, they create a robust quality assurance process for secure and reliable deployments in your CI/CD pipeline.
Apply Canary Deployment or Blue-Green Deployment (if Need Be)
You and your team should decide which deployment method will be most beneficial to your organisation. What is the best strategy to deploy in your specific business case? Let’s look at a few common tactics.
Blue-Green Deployment
This deployment technique uses two identical environments: “blue” (staging) and “green” (production). QA and user acceptance testing are often performed in the blue environment, which contains new versions or updates.
Blue-green deployment is simple, quick, uncomplicated, and easy to set up. In the event of an issue, rollback allows you to swiftly return traffic to the previous environment. Thus, this method is less dangerous than others.
Remember, recreating a production environment can be difficult and costly, so make sure it meets your requirements.
Canary deployment
Within this deployment method, you gradually roll out an application or service to a subset of users. All infrastructure is changed in tiny increments.
Canary deployments enable organisations to test in production with a fraction of real users while comparing multiple service versions side by side. It costs less than the prior technique since it eliminates the need for two production environments. It is also quick and safe to roll back to a prior version of a program.
However, programming a canary release can be complicated. Manual verification or testing takes time, and monitoring and instrumentation for testing in production may necessitate extra research.
Also, you can’t switch to a newer version in a second (as is typical for blue-green deployment). You need to account for ramp-up time because the latest version will remain fully accessible for some time before the deployment is completed.
Roll Back a Failed Deployment (if Need Be)
When creating CI/CD pipelines, it’s common to overlook the option to roll back the deployment. Let us repeat: your CI/CD should not mark the deployment as “finished” as soon as it is sent to production. If you can automate the deployment, why not automate the safety features that will roll back the deployment in the event of an error, too?
Allow your CI/CD to watch your newly deployed application for a few minutes after deployment and look for issues. If it detects any, simply redeploy the previously operating version of the application.
If you follow our first best practice and include many tests in your pipelines, you should not encounter many of these scenarios; nonetheless, no test is perfect, and there is always the possibility that something will not operate as planned.
Without a revert option in your CI/CD pipeline, recovery time will be significantly longer because you will likely have to manually start the workflow again. In some circumstances, you will have to wait for all the steps to finish first. You can eliminate those extra procedures by enabling the ability to roll back a deployment.
Infrastructure as Code
CI/CD relies on continuous automation and monitoring of the application life cycle, from testing and integration to delivery and deployment. Throughout all this, the automated environment must be consistent. When the development team delivers apps or configures environments in one way and the operations team deploys and configures in another, automated application deployments fail. This is where Infrastructure as Code comes to the rescue.
Infrastructure as Code (IaC) refers to the management and distribution of infrastructure using code rather than manual methods.
IaC generates configuration files that include your infrastructure specifications, making it easy to change and distribute configurations. It also guarantees that you provision the same environment each time. IaC simplifies configuration management by codifying and documenting your configuration standards, allowing you to avoid undocumented, ad hoc configuration changes.
To sum up, the benefits of IaC are cost reduction, increased deployment speed, reduced errors, improved infrastructure consistency, and the elimination of configuration drift.
CI/CD Security Checklist

Black-hat hackers are always attempting to decipher new encryption codes and identify security weaknesses. Cyber attackers utilise the following security threats to jeopardise your CI/CD pipeline:
- Insecure codebase;
- Security Misconfigurations;
- Using faulty third-party libraries;
- Sprawling secrets.
Next, we’ll look at best practices and approaches for improving CI/CD pipeline security.
1. Provide Vulnerability Report
The first item on the checklist is a vulnerability report for both the pre- and post-build stages.
Applications are becoming more vulnerable as open-source tools and libraries, as well as containers, gain popularity. As a result, security testing, which analyses source code and finds security flaws, should be automated. Without sufficient checks, applications can become vulnerable to attack while still in production.
This is where Static/Dynamic Application Security Testing (SAST/DAST) comes in. It is a popular security testing method for identifying source code and binary vulnerabilities.
In general, DevSecOps must strive to fully automate security scanning by integrating with CI/CD pipelines.
For example, they can create a step in the Spinnaker pipeline to automate static analysis with third-party tools such as SonarQube. However, implementation is only one half of the equation; a comprehensive understanding of vulnerabilities and code risk across the organisation’s projects and apps is crucial for the DevOps team.
The post-build step is critical. This is where software artefacts emerge, making it a breeding ground for security vulnerabilities. Vulnerabilities, insecure dependencies, and unauthorised access can all enter during this phase, putting your applications in danger. Addressing security vulnerabilities at this point is critical for ensuring your applications’ integrity and safety before they go live.
2. Deliver Bill of Material (DBOM) Report
The DevSecOps team’s second checklist item is DBOM. This one is getting increasingly popular for speedy software delivery. The Delivery Bill of Material (DBOM) is a comprehensive report on the software supply chain and security management during the software delivery process.
The DBOM contains such information as security risk reports, quality and performance reports, testing results, the application’s development and deployment history, the tools used to provide the application, and more.
The major reason DevSecOps should keep a DBOM report in the CI/CD is to increase transparency for all stakeholders at each delivery stage. The DBOM can be shared with the following stakeholders: DevOps, the Security or GRC team (or compliance management), Application engineers, the Delivery team, or the Operations team.
A DBOM facilitates the systemic sharing of risk assessments by tracking metadata, such as software components, and linking it to other information when an application moves to production. A DBOM report assists organisations in successfully and efficiently consuming application status reports throughout the software supply chain.
The DevSecOps team should understand all the pieces that make up a DBOM. It holds the code component that serves as the foundation for the app, as well as for its current risk status.
The report gives information on an application component and its possible hazards at every stage of software delivery, including code, build, test, deploy, and production.
3. Software Bill of Materials (SBOM) Report
The third item on the DevSecOps checklist is SBOM. A Software Bill of Materials (SBOM) provides those who produce, purchase, and operate software with additional licence information that improves their understanding of the supply chain, allowing for a variety of benefits, most notably the ability to track known and newly emerging vulnerabilities and risks.
According to a report from the National Telecommunications and Information Administration (NTIA), a SBOM is a formal record that contains the specifics and supply chain links of numerous components utilised in software development.
In many organisations, DevOps teams employ SBOM to improve software transparency. Large corporations, such as Google, Apple, and Cisco, treat SBOM as part of their Delivery Bill of Materials (DBOM).
4. Restrict Code Repository Access
Continuous integration relies largely on code repositories and version control systems to host and share the codebase. These platforms are beneficial to collaboration, but attackers can wreak havoc on your codebase if it is open-source and has weak security.
If a security vulnerability exists in the most recent codebase version, it will undoubtedly be present in the live application. As a result, it is critical to encrypt your keys and avoid embedding your secrets in application code. Instead, use a secret manager like Doppler to encrypt and safely distribute your keys.
5.Use Audited Code
With so many free tutorials and application source codes accessible today to cover almost any application use case, many developers simply copy and paste third-party source codes without first screening and auditing them. Using unscanned source code may result in defects in your codebase. The repercussions of taking the “if the code compiles, then leave it” approach can be severe. Third-party tools, unsafe code, and non-audited components can all contribute to CI/CD security vulnerabilities.
CI/CD – How to Measure Success?
DevOps teams can’t know how well their CI/CD best practices are working unless they analyse them. Metrics are critical for improving system performance and identifying areas where you can contribute value. They also serve as a foundation for monitoring the effectiveness of any modifications made.
We recommend you examine the following metrics to understand if you’re on the right track with your CI/CD best practices.
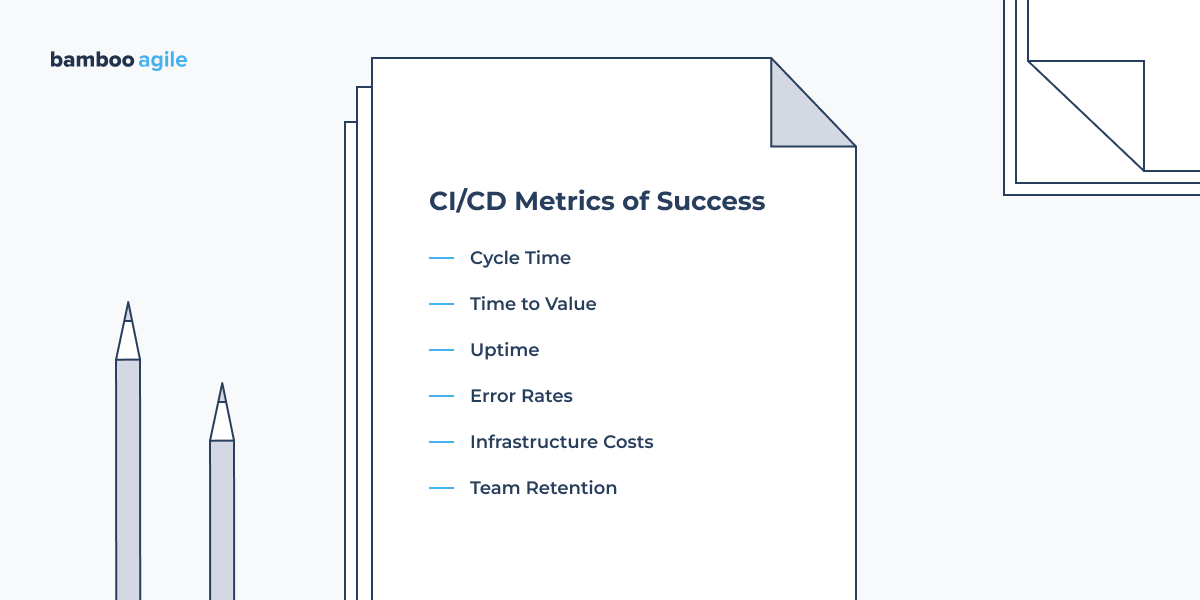
Cycle Time
This refers to how long it takes to launch a working application after code development begins. Determine the average life cycle time by measuring the number and length of your development process steps. This measure will provide information about the overall development time and any existing bottlenecks.
Time to Value
This is the amount of time it takes to release the created code. Integration, testing, delivery, and deployment should take from minutes to a few hours to complete. If it takes days to proceed with a build through the CI/CD pipeline, time to value is lost, and the process should be improved.
Uptime
Uptime measures stability and reliability, as well as whether everything works properly. It is one of the operations team’s top priorities. When the CI/CD method is automated, operations managers may devote more of their attention to system reliability and less to workflow difficulties.
Error Rates
Application errors are unavoidable, and their rates need to be monitored. Tracking them is critical since error rates might signal not just quality difficulties, but also ongoing performance and availability issues. If uptime and mistake rates appear to be high, this may indicate a common CI/CD difficulty across the development and operations teams.
Infrastructure Costs
Infrastructure costs are significant for cloud-native development. Deploying and managing a CI/CD infrastructure can be expensive if not done correctly. Cloud providers will evaluate the costs of network gear, infrastructure maintenance, and labour when determining how much to charge.
Team Retention
It’s no surprise that when a developer, or anyone for that matter, feels valued and fulfilled, they’re more likely to stick around. When teams work effectively together and understand how to collaborate, retention is more likely to occur. On the other hand, developers may be reluctant to speak up if they are dissatisfied with the way things are going, but looking at retention rates might assist in discovering potential issues.
Benefits from Following CI/CD Best Practices
When best practices are implemented, the benefits of CI/CD can be felt throughout an organisation. Teams collaborate more effectively and achieve their objectives, from HR to operations. Establishing metrics for CI/CD performance can provide insights into development while also affecting many other elements of the business.
An efficient CI/CD pipeline can be transformational for DevOps teams. Here are some of the main benefits.
Developers don’t fix problems, they write code. Fewer tools and toolchains imply less time spent on maintenance and more time spent developing high-quality software applications.
The code is in production. Rather than waiting in a queue, code is deployed into the real world almost immediately. This also results in happy developers.
Developers have the time to concentrate on fixing business issues. A streamlined CI/CD workflow allows developers to focus on what is important rather than being distracted by problem code, missing handoffs, production issues, and so on.
It is easy to innovate. To keep ahead in today’s competitive world, organisations must use all of their available resources. A well-built CI/CD workflow simplifies, accelerates, and secures software development, giving DevOps teams more time and energy to think outside the box.
It helps attract and retain talent. It’s a very competitive labour market, and DevOps talents might be difficult to impress. Nothing says “We take our DevOps team seriously” like an organisation that has invested in CI/CD technology and practices.
Everyone does their best. Each of the development, operations, security, and testing teams plays an important role, and CI/CD helps to clearly define those roles.
CI/CD Security Risks
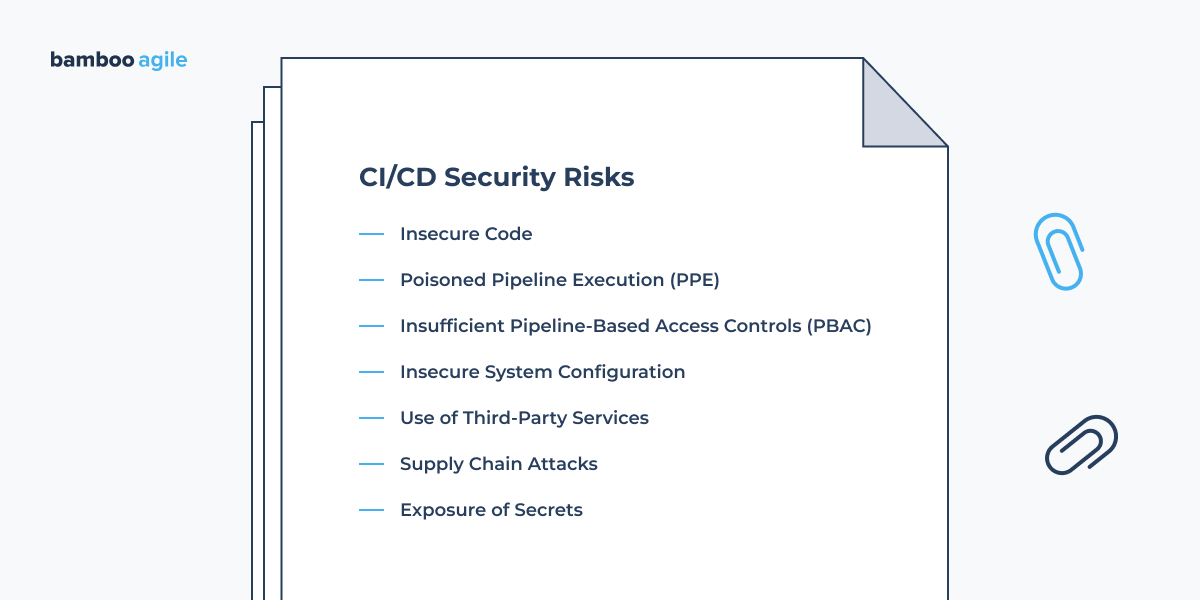
Insecure Code
The current development lifecycle is intended for speedy development and delivery. To achieve this goal, CI/CD pipelines are increasingly using open-source components and third-party connectors. However, rapid development without effective security might introduce flaws and expose the pipeline to serious hazards.
Improper third-party integration and a lack of code scanning for source code components might lead to vulnerabilities in your CI/CD process. Failure to follow code security best practices can greatly increase the attack surface. Buffer overflows, format string vulnerabilities, and incorrect error handling are all examples of common code vulnerabilities.
Poisoned Pipeline Execution (PPE)
PPE is a technology that allows threat actors to poison the critical infrastructure pipeline. It was presented by Cider Security’s head of research, Omer Gil. The approach manipulates the build process by taking advantage of permissions in source code management (SCM) repositories. Injecting malicious code or commands into the build pipeline configuration poisons the pipeline, causing malicious code to run during the build process.
Insufficient Pipeline-Based Access Controls (PBAC)
PBAC grants or restricts access to resources and systems within and outside the execution environment. Pipeline execution nodes employ these resources to conduct a variety of tasks. However, if malicious code enters the pipeline, threat actors can employ insufficient PBAC risks to misuse pipeline permissions and move laterally within or outside of the CI/CD system.
Insecure System Configuration
CI/CD systems have multiple infrastructural, network, and application configurations. These configurations have a significant impact on your CI/CD pipeline’s security posture and susceptibility to cyberattacks. This is why threat actors are actively looking for CI/CD misconfigurations and vulnerabilities to exploit.
Use of Third-Party Services
Modern CI/CD pipelines frequently include a large number of third-party integrations to support speedy development and deployment. However, the incorrect use of third parties can bring security flaws into the pipeline. Securing the use of third-party services often entails putting in place rules that provide governance and visibility, such as role-based access restrictions.
Supply Chain Attacks
Software programs frequently rely on dependencies for essential functioning, whereas CI/CD distributes source code and binaries to many public repositories. This supply chain covers a wide range of partners, including organisations, individuals, resources, technologies, and activities related to the development and sale of software. So supply chain attacks target vulnerable individuals to compromise others in the chain.
Exposure of Secrets
CI/CD tools require various secrets to obtain access to sensitive resources such as databases and codebases. Secrets are necessary for tool authentication as well as participation in the build and deployment process to verify that deployed resources are accessible. However, the increased consumption of secrets by CI/CD pipelines complicates the secure storage, transmission, and auditing of secrets.
Bamboo Agile’s Opinion
We’ve asked Sergey Botyan, DevOps Lead at Bamboo Agile, to share his thoughts about CI/CD processes.

CI/CD is a key concept in modern software development, aimed at accelerating and automating deployment processes.
I recommend:
- implementing strong version control;
- automating testing at all stages to ensure code quality and safety;
- using containerisation to simplify deployment and ensure consistency in the environment.
Additional attention should be paid to the management of secrets and access to minimise security risks. Don’t forget the importance of monitoring and logging during the CI/CD process to quickly identify and resolve issues in your production environment.
It is also worth using blue/green or canary deployment strategies to minimise risks when rolling out new versions of the application. It helps to ensure uninterrupted service for users.”
Conclusion
A pipeline may appear to be unnecessary overhead, but it’s worth the setup costs for increased productivity, a better developer experience, faster development cycles, and more delighted users. Without CI/CD, you have no idea how your project is progressing and you can’t maintain momentum or generate software at a predictable rate.
We hope these recommendations will assist you in establishing and optimising your first CI/CD workflow. However, if you are looking for an experienced DevOps service company or a custom software development team, consider Bamboo Agile as an option for partnership. Contact us to level up your processes across the board.