Introduction
The development process of a secure Fintech application is complex, time-consuming, and most importantly, expensive. If you don’t have an experienced team with an awareness of the Fintech security requirements, this process is almost impossible.
Understandably, modern Fintech applications deal with lots of personal and business data every day. That’s why such solutions require security of the highest level, starting from the idea stage, and being present throughout the entire lifecycle of the application.
Cybersecurity statistics and trends
Cybersecurity is now considered a “must-have” for internet users. It’s comparable to a home alarm or an automatic lock system. You wouldn’t leave your front door exposed to robbers, so why would you leave your computer accessible to hackers? Especially if you own a business, you don’t want any of your personal information to end up on the dark web.
As a result, you’ll need to invest in firewalls, antivirus software, and possibly even cyber insurance. Here is the most recent cyber security data to assist you in preparing your defence against hackers:
- The global cybersecurity market, in terms of revenue, topped $173.5 billion in 2022 and is expected to grow at an 8.9% CAGR to exceed $266.2 billion by the end of 2027;
- Global cybersecurity spending (including enterprise goods and services) is expected to expand by 13.2% by 2023, continuing to be a key growth sector for channel partners. In the best-case scenario, total spending in 2023 is estimated to reach US$223.8 billion, with growth in cybersecurity service delivery exceeding product shipments.
- The global cyberinsurance market was worth USD 13.54 billion in 2022 and is expected to be worth more than USD 91.22 billion by 2031, with a CAGR of 23.78% over the forecast period.
Now, what are the top cybersecurity trends? According to Gartner, they are:
- Threat exposure management: the process of identifying, assessing, and mitigating risks to an organisation’s IT systems and data;
- Identity fabric immunity: an approach that focuses on protecting identity systems from attack by applying digital immunity principles (continuous monitoring, rapid remediation, and zero trust) to identity systems;
- Cybersecurity validation: the process of verifying that security controls are working as intended and that they are effective in protecting an organisation from cyber threats;
- Cybersecurity platform consolidation: the process of combining multiple security products into a single platform. This can help to improve efficiency, reduce costs, and improve security posture;
- Security operating model transformation: the process of changing the way an organisation manages its security operations. This can involve changes to the people, processes, and technologies used to protect the organisation from cyber threats;
- Composable security: an approach that allows organisations to combine different security products and services to create a customised security solution that meets their specific needs;
- Human-centric security design: an approach that focuses on the human element of security. It means designing security solutions that are easy to use and understand, and that do not create unnecessary friction for users;
- Enhancing people management: the process of developing and implementing strategies that improve the effectiveness of people in cybersecurity roles by providing employees with the training and resources they need to be successful, creating a positive work environment, and recognising and rewarding employees for their contributions;
- Increasing board oversight: the process of ensuring that the board of directors is aware of cybersecurity risks and is taking steps to mitigate them.
What are Fintech-associated risks?
Security measures should be a critical component of development, particularly in the case of Fintech. You cannot afford to threaten your clients’ privacy or consumer trust. There are numerous security flaws that credit unions, financial organisations, and banking institutions face. Here are the most common ones.
No unified app ownership
When it comes to defending mobile banking services in the Fintech industry, app ownership is one of the most dangerous weaknesses you need to account for. There are often two app owners: one is a peripheral owner and the other acts on the behalf of the bank. The app is also owned by the bank’s IT department. Aside from that, an external business is working on the mobile banking apps and the governance of their APIs.
Because the three owners described above share accountability, this style of ownership creates major security concerns. As a result, there is a great probability of something going wrong at any time.
Risky data storage
Every mobile app you use saves your data in some form. Because the data in the Fintech services industry is so sensitive, storage solutions must be exceedingly secure to avoid vulnerability. This is the first line of defence against financial data leaks, programme code loss, and unsecured storage space. If your internal storage has a vulnerability, hackers can obtain direct access to your sensitive data and use it to their advantage.
Failure in communication
Mobile apps must communicate with external data sources such as NFC, Bluetooth devices, servers, various permission processes, and authentication tokens. You cannot avoid this contact; otherwise, the software will not work properly. However, there is always the risk of such transactions being intercepted. So companies need to employ extra protection measures for data in transit.
What to take into consideration while developing a Fintech application
Secure infrastructure
During the Fintech application development process, it’s very important to use a reliable and secure IT infrastructure to avoid endangering your user’s sensitive data. If your app has to use a public cloud, think of choosing a trusted cloud service provider that meets the latest cloud computing security standards.
There are a lot of such standards, but it’s very important to mention the following:
- ISO-27001 / ISO-27002
ISO-27001 contains the Information Security Management System (ISMS) specification. ISO-27002 describes the controls that can be implemented in accordance with the ISO-27001 standard. Compliance with the ISO-27001 standard shows your customers that your organisation is serious about information security and implements the best practices for protecting information. - ISO-27017
This is an extension to ISO-27001 that includes clauses related to information security in the context of the cloud. Compliance with ISO-27017 should be considered alongside ISO-27001. - ISO-27018
This standard refers to the protection of personally identifiable information (PII) in public clouds acting as PII handlers. This standard specifically targets public cloud providers such as AWS or Azure.
The AWS Enterprise Cloud has everything to counter massive DDOS attacks. It will also provide fast recovery in case of disruption.
For financial institutions that build their Fintech apps based on cloud infrastructure, it is highly important to ensure that the cloud service providers adhere to the same standards that they use internally.
Cybersecurity requirements for Fintech applications can be different depending on the company’s location:
- For the European Union – GDPR, PSD2, eIDAS
- For the United Kingdom – GPG13, FCA
- For Japan – APPI
- For South Korea – PIPA
- Worldwide – PCI DSS, ISO/IEC 27000
Application logic security
Building secure application logic means the integration of security at every stage of the application’s performance. Every aspect of your future application needs to be protected from potential threats.
Consider the following security actions:
- Requiring users to set complex passwords;
- Complicated authentication, e.g., two-factor;
- Keeping a datalog of all the user’s actions, their geolocation, IP addresses, and device info;
- Keeping users’ information encrypted to avoid attackers getting personal data as it is;
- Monitoring of transactions and blocking suspicious ones;
- Doing regular backups;
- Practising security rehearsals.
Secure code
Fintech application code should be easily portable between devices and include algorithms to easily detect any problems in the case of a breach or an attack. At the very least, the process of updating the code has to be simple.
The best practices for writing secure application code include input review and the validation of any data that is sent to external networks. Access should be granted only to the basic functions of the application, rules have to be defined clearly, and all the necessary steps have to be taken to ensure the protection of sensitive data. And don’t forget about SQL injection protection – your Fintech app can still be hacked that way.
Web-server security
Since the webserver is the most common target for external attacks, it is now common practice to secure the data with an HTTPS SSL certificate. Most popular browsers will warn users when a website has no such certificate, so you obviously cannot skip this step and remain a trustworthy service.
Another common practice is using a VPN. It complicates the setup stage, but this step is worth your efforts because access will only be given to the hardware with a valid public key.
API security
Most users run Fintech applications on mobile devices. Such apps use application programming interfaces (APIs) to interact with their backend. That’s why APIs are also regular targets of attacks, and you have to keep them secure to protect the rest of the application.
Identification, authentication, authorisation
The identification, authentication, and authorisation system should serve as a reliable barrier against any invasion or suspicious activity. Your authentication methods should not be limited to just passwords. Combine them with SMS verification or one of the latest biometric authentication methods such as a fingerprint or retinal scan.
During authorisation, the application identifies the user as a person who is either allowed or not allowed to perform certain tasks. Ideally, user rights should be limited to a certain set of actions and commands.
There are several different authentication technologies, including:
- One-time password system
The app automatically generates an additional password with a limited expiration date every time the user wants to log in to an account or complete a transaction. - Mandatory password change
FinTech organizations can significantly reduce security risks by forcing customers and employees to change passwords on a regular basis. Many online banking applications require you to reset user account passwords every three or six months. - Monitoring
With the help of a tracking system, you can analyze suspicious activity (for example, failed logins) to identify cases of unauthorized access. In addition, this solution can prevent data leakage by locking the account after several suspicious transactions. - Short log-in sessions
The shortened session time is useful for protecting financial data. The reason is that even if a hacker gains access to the account, he will have limited time to collect the important data. - Adaptive authentication
Multi-factor authentication is not a panacea. In fact, it can even increase the risks of data leakage (for example, if a hacker manages to clone your smartphone). But with adaptive authentication, your system will analyze user behaviour to detect suspicious activity. As a result, your platform will receive additional protection for financial data and personal information.
Data encryption techniques
You have to encrypt your user’s personal information (name, address, social security number) and their financial data such as credit card numbers and payment history, as well as any other information that may be obtained upon receipt of a particular financial service.
Encryption is essential to protect data during transmission when it is highly vulnerable and can be easily snapped up. Secure data transmission involves the use of various encryption algorithms; for example, the US federal government uses AES, which is currently considered the most secure.
You can protect critical data with complex encryption algorithms, such as:
- RSA
A highly secure asymmetric algorithm with a private encryption key and a public encryption key. - Twofish
A freeware algorithm that encrypts data into 128-bit blocks. - 3DES
The preferred encryption method to secure credit card PINs. Triple DES divides data into 64-bit blocks and cyphers each one three times.
Payment blocking feature
One way to prevent fraud is to point out suspicious activity. Use something that will be significantly different from the usual user activity, for example, unusually large amounts of money transferred from unusual locations.
To protect the user from possible fraud, implement a payment blocking function in your application. This feature will provide immediate blocking of payments after something, unlike the user’s normal activity, is detected.
Security testing
Creating secure Fintech solutions requires meticulous testing at each of the development stages.
It is common practice to conduct “penetration testing” – launching your own simulated attacks to discover vulnerabilities in your application. Needless to say, continuous and thorough testing should be an integral part of the development process. It’s possible to hire security testers to create high-quality, attack-resistant code.
Also, one of the practices is to simulate potential emergencies and create ways of handling them for the personnel.
Establish clear and consistent access rights to prevent data leakage at every stage of the development process, ask your employees to sign an NDA, and use corporate equipment on your premises.
Today, many financial companies are ISO-27001-certified. The certification and confirmation process is complex, but having that certificate will mean that your company is using truly top-notch security practices.
Code obfuscation
Cybercriminals can clone a Fintech app to steal personal user data while remaining undetected. To prevent app copying, Fintech companies should consider code obfuscation. Encrypting the code, removing revealing metadata, labelling classes and variables with meaningless labels, or adding useless or meaningless code to an application binary are all examples of code obfuscation.
AI&ML to track user transactions
To prevent various cyber assaults, the Fintech app can keep track of all significant user behaviours such as user IDs, device data, IP addresses, geolocation, and transactional activity. Artificial Intelligence and Machine Learning can be used to maintain a constant eye on users’ behaviour to detect common trends and odd behaviour. One example would be to block suspicious transactions from an unknown or odd IP address.
Tokenisation
Tokenisation is the process of replacing vulnerable data with a newly produced random string of symbols known as tokens. Only authorised users will have access to a one-of-a-kind database known as the ‘token vault,’ which retains all relationships between the original data and the produced token. Tokenisation makes PCI compliance easier by safeguarding data within organisations and online transactions.
Regular data backup
Data loss isn’t always the consequence of an external danger; it can also be the result of human error or technology failure. Making a backup of important data keeps it from being completely lost. To save as much altered data as possible, make sure that key files are periodically backed up, including edited and changed data.
Vulnerabilities monitoring in the installed packages
Fintech apps frequently make use of third-party software vendors. But third-party apps may contain vulnerabilities and weaknesses that fraudsters might exploit, making the whole system rife with security issues. Hackers can carry out a supply chain attack, in which they compromise a third party to gain access to data.
It’s better to screen third-party suppliers before using their services and monitore them frequently during installation. It will assist you in identifying vulnerabilities in your project, revealing which areas are affected and what needs to be fixed.
What to expect if you ignore Fintech security?
Whether due to a blackout or ransomware, your organisation is still responsible for preserving your customers’ data if it is lost or corrupted. You must consider the risk of every piece of information being handled during financial transactions.
Thibald Carty, CCO at ConnectPay says:
“Now it’s possible to prevent fraud at the same — or even higher — efficiency with fewer people simply by utilising the appropriate tools and automation.”
Let’s have a look at some of the potential hazards and see what you should be especially wary of.
Identity theft
This problem arises when someone steals personal or financial information and gains access to your, your colleague’s, or your client’s private data, such as bank account passwords. Given the fact that anyone can be a victim of identity theft, it’s difficult to overlook the need of distributing access and specific functions within a corporate network among employees. Identity theft is also likely to trigger a cascade of further problems, such as phishing or spoofing, which can result in massive data and financial losses.
Abuse of a client’s trust
Good news is not likely to spread as quickly as bad news. If your clients are pleased with your Fintech app, they will undoubtedly continue to use it. Furthermore, they are inclined to tell their friends about it. But consider what happens if a customer’s data is compromised: not only will you lose the trust of your current client, but also of other potential consumers.
While improving financial security takes time and money, regaining trust requires significantly more effort.
Data loss
If a fraudster can read the data, it can be stolen, lost, or exploited. And if the stolen information is in plaintext or poorly encrypted, a hacker does not need to exert much effort to read and utilise it. Overall, it results in a breach of customer trust, reputational concerns, and profit losses.
These are the three key security issues. The bad news is that every system can be hacked, but the good news is that the magnitude of losses – such as the time and money required to recover – is determined by the strength of your financial security.
Fintech app security technologies to use
Secure Access Service Edge (SASE)
SASE (Secure Access Service Edge) is a network solution that combines VPN and SD-WAN expertise with cloud-native security measures such as secure internet gateways, cloud security brokers, firewalls, and zero-trust network access. Furthermore, the SASE architecture aids in network traffic analysis and detects dangerous digital data in fraudulent transactions, ransomware, and other similar situations.
Here is what Safi Raza, Director of Cyber Security at Fusion Risk Management is saying about this technology:
“SASE has been proven effective in securing the remote workforce during the pandemic. It is a cloud-based architecture that delivers network and security services to protect users, applications, and data.”
Artificial Intelligence (AI)
Fintech organisations are increasingly utilising machine learning to properly comprehend financial data and security systems. AI algorithms can help detect malicious data streams, intrusions, and other dangers by tracking network traffic databases. AI also aids in the deep analysis of customer data to determine future clients’ strengths, shortcomings, and so on. This helps businesses prevent hazardous customers as well as future criminal transactions.
Digital currency
Cryptocurrency, or digital currency, is currently at its height. It is an essential component of blockchain-based decentralised finance frameworks. The ease, comfort, and speed with which digital transactions may be done astound the industry, but the integration of digital currency security is the most advantageous part for the Fintech business.
Regulatory technology
RegTech, or Regulatory technology, is a type of modern technologies that assist businesses in managing regulatory compliance. This tech, among other things, provides artificial intelligence, machine learning, and blockchain technology to help organisations comprehend regulatory requirements and monitor their content to maintain Fintech security compliance.
What to expect in the future?
Regulatory sandboxes
Many countries have created regulatory sandboxes, which are test environments where Fintech companies can conduct experiments under regulatory supervision. Some countries’ regulators (particularly the FCA in the UK) allow Fintech companies to conduct these experiments with real customers.
The United Kingdom’s Financial Conduct Authority (FCA) was the first agency to introduce a regulatory sandbox in 2016. Since then, over 70 jurisdictions around the globe have copied the FCA’s model. In the United States, several state legislatures have attempted to emulate the U.K.’s success by creating their own state-level sandboxes, but these efforts have had mixed results.
One of the challenges facing state-level sandboxes is that they are more limited in the kinds of benefits they can offer participants than national supervisors like the FCA. For example, Arizona’s sandbox companies can test their products for up to two years and serve as many as 10,000 customers before needing to apply for a formal licence. However, they cannot offer financial incentives to customers or participate in government procurement programs.
Finance-as-a-service regulations
The catalogue of APIs is growing and new regulations are emerging with every new advancement in Fintech. So the Finance-as-a-Service movement has seen significant growth in recent years, and this trend is expected to continue in 2023. Like other X-aaS products, Finance-as-a-Service is provided by unregulated organisations that offer regulated financial products.
The key changes that are expected for the FaaS market in 2023:
- The growth of embedded finance. Embedded finance is the integration of financial services into non-financial products and services. This trend is expected to grow, as businesses look for new ways to reach their customers and offer them financial services that are convenient and easy to use.
- The rise of open banking. Open banking is the sharing of financial data between banks and third-party providers. This trend allows businesses to offer their customers a wider range of financial services and products, so it’s expected to continue to grow in 2023.
- The increasing use of artificial intelligence (AI) and machine learning (ML). AI and ML are being used to automate tasks in the FaaS market, such as underwriting and risk assessment. This is helping to make FaaS more efficient and cost-effective.
- The growing importance of security and compliance in the FaaS market. As FaaS becomes more popular, businesses are becoming more aware of the need for security and compliance. This drives the development of new security and compliance standards for the FaaS market.
Regulations of open banking
Open banking is in high demand, and industry leaders note that the data-sharing framework will become integral to the countries that are introducing it. Open banking has already established itself in Europe and is making significant headway in countries such as Australia and Canada. However, the United States is in no hurry to enact such regulations.
The Consumer Financial Protection Bureau (CFPB) has issued an Advance Notice of Proposed Rulemaking (ANPR) that solicits information from the public on how consumers’ access to their financial records should be regulated. ANPR is considered to be the first step towards establishing the formal regulation of open banking in the United States.
Looking at this progress, governments and regulators will continue to enact laws and frameworks for open banking. In turn, banking data will continue to gain more layers of protection with the help of financial innovators worldwide.
Regulations of online payments and SCA
Since January 1, 2021, online card payments in the EU must go through the Secure Customer Authentication (SCA) protocol of the second Payment Services Directive (PSD2). While this security feature is good news for consumers, merchants may struggle, as the SCA increases their shopping cart bounce rate. Survey showed that 33% of UK consumers have already experienced inconvenience in their shopping experience that made them abandon their shopping cart.
As a result, merchants and other online retailers are seeking alternative payment methods, such as Secure Corporate Payment (SCP), Transaction Rysk Analysis (TRA), Low Value Payment (LVP), Merchant Initiated Transaction (MIT), Recurring Payment (RP), SCA Delegation (SD), and Trusted Merchant (TM), to process transactions securely without compromising the user experience.
Tips for users on how to use Fintech apps securely and safely
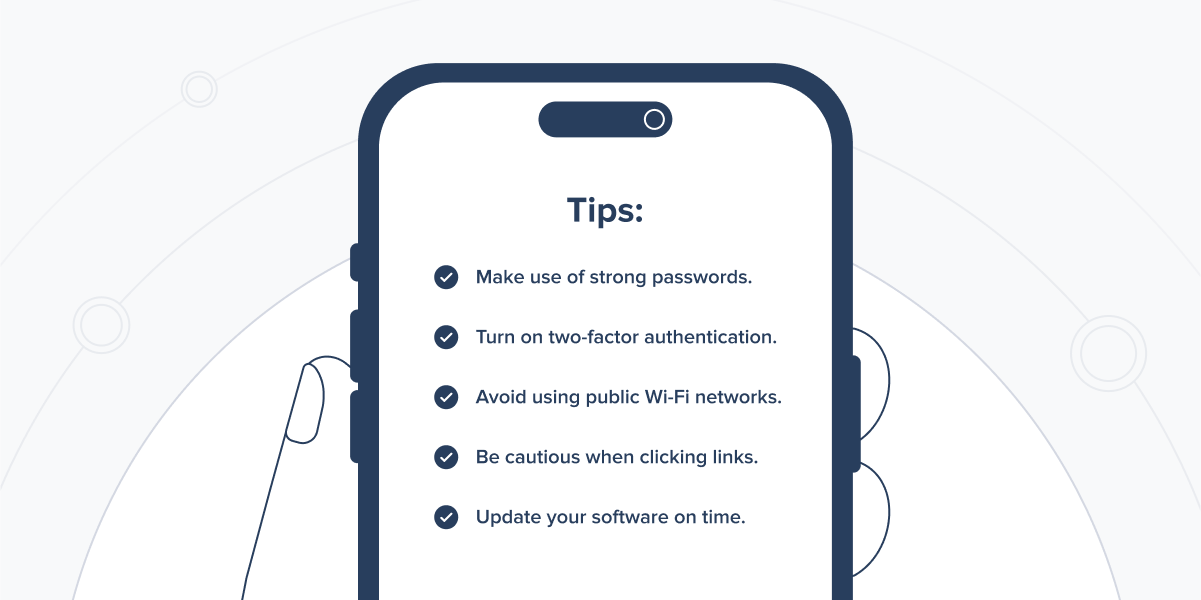
In addition to assisting users in achieving more data privacy and protection online, we must also take action to protect ourselves.
Here are some security precautions for using Fintech apps:
- Make use of strong passwords. Use a strong password when creating your account. This entails combining letters, numbers, and symbols. It is also advisable to update your password frequently.
- Turn on two-factor authentication. Two-factor authentication can aid in the protection of your account against unauthorised access. Users will be required to submit two pieces of information to log in. The first is typically a password, while the second can be a PIN, biometric data, or a code sent to the user’s phone.
- Avoid using public Wi-Fi networks. Public Wi-Fi networks are insecure and readily compromised. If you need to use the internet while you’re out and about, consider using your data plan instead.
- Be cautious when clicking links. When clicking links in emails or on websites, use caution. Cybercriminals frequently utilise bogus links to obtain personal information from consumers. Only click on links that you are confident in.
- Update your software on time. Install the most recent security updates from the manufacturer to keep your software secure. This will aid in the protection of your device against malware and other online threats.
Examples of cyberattacks on the Fintech industry
Despite the big differences in scope and environment, many of the attacks against Fintech organisations could have been avoided with one simple change: improved security architecture.
Most cyberattacks succeed as a result of the victim’s lack of caution, and those problems require a multi-layered approach Here are some examples of the biggest cyberattacks in the Fintech industry.
Equifax
In this attack, hackers exploited a vulnerability in Equifax’s web application software to gain access to the sensitive personal information of over 143 million individuals, including names, social security numbers, birth dates, addresses, and in some cases, driver’s licence numbers. The breach resulted in a $1.4 billion loss.
The lesson of this cyberattack: ensure that your systems are up-to-date with the latest security patches and that you have implemented proper access controls.
JPMorgan Chase
This attack involved one of the largest US banks, with hackers stealing the personal information of over 76 million households and 7 million small businesses. The breach was caused by a flaw in the bank’s website that allowed hackers to gain access to sensitive data. To avoid such incidents in the future, companies should conduct regular security audits and penetration testing to identify vulnerabilities in their systems.
SWIFT
Hackers targeted the Society for Worldwide Interbank Financial Telecommunication (SWIFT), a global financial messaging system used by banks to transfer trillions of dollars every day. The attack involved the theft of $81 million from the Bangladesh Bank’s account at the Federal Reserve Bank of New York. The breach was caused by weak security controls at the bank and the use of outdated software. This attack could be prevented by prioritising security and investing in the latest security technologies.
Capital One
In this attack, a former employee of Amazon Web Services (AWS) gained unauthorised access to Capital One’s data stored in the cloud, resulting in the theft of the personal information of over 100 million customers. The breach was caused by a misconfigured firewall in the cloud infrastructure. The lesson of this attack – ensure that your cloud infrastructure is properly configured and that you’ve implemented proper access control.
Target
This attack involved the theft of credit and debit card information of over 40 million customers of the US retail giant, Target, and 70 million of their customer records. The breach was caused by a vulnerability in Target’s payment system, which allowed hackers to install malware on the company’s point-of-sale systems. To avoid such incidents in the future, companies should implement strong security controls and regularly monitor their payment systems for any signs of unauthorised access.
Conclusion
As you can see, ensuring Fintech app security is a complex process requiring very specific knowledge and skills to deal with highly sensitive data. And it is highly important to have the help of qualified and experienced professionals when developing such a solution. When looking for a partner like that, consider Bamboo Agile. The development team has significant experience in developing secure Fintech applications and knows how to meet all the requirements firsthand.
Contact us today to get a free consultation about your FinTech project and the ways to ensure the safety of all your sensitive data.